An Overview of CMMC
As the requirement for the Cybersecurity Maturity Model Certification (CMMC) is just around the corner, it is critical for organizations with U.S. defense contracts to understand their requirements and be prepared to act when the time comes. The scope of the framework is to protect Controlled Unclassified Information (CUI)—data that is sensitive to the Department of Defense (DoD) but does not rise to the level of “classified” information.
On December 26, 2023, DoD released the long-awaited proposed rule outlining the CMMC program, providing insight into DoD’s intention for the future of the CMMC framework. As written, the proposed rule would require approximately 80,000 defense contractors that process, store, or transmit CUI to undergo assessment by a Certified Third-Party Assessment Organization (C3PAO) and demonstrate compliance with the 110 security requirements defined within National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171. Additionally, contractors handling Federal Contract Information (FCI) would be required to complete an annual self-assessment.
Spanning a wide variety of industries, DoD’s supply chain, the defense industrial base (DIB), is estimated to be more than 200,000 organizations. It is expected the number of organizations that require a third-party assessment by a C3PAO approaches 80,000 organizations.
Forvis Mazars wants to arm you with the knowledge necessary to head into CMMC compliance confidently.
CMMC Maturity Levels
| CMMC Model 2.0 | Model | Assessment | Details |
|---|---|---|---|
| Level 3 Expert | 110+ practices based on NIST SP 800-172 | Triennial government-led assessments |
|
| Level 2 Advanced | 110 practices aligned with NIST SP 800-171 | Triennial third-party assessments for critical national security information; Annual self-assessment for limited programs |
|
| Level 1 Foundational | 17 practices | Annual self-assessment |
|
Source: U.S. Department of Defense CMMC MODEL
A large percentage of organizations subject to CMMC requirements will fall under Level 2, which requires implementation of 110 security controls defined by NIST SP 800-171 Revision 2. At this time, those contractors required to achieve CMMC Level 3 remain unclear; however, DoD has indicated it will be a limited number of contractors associated with special programs. Level 3 assessments will be performed by the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC) and not by C3PAOs.
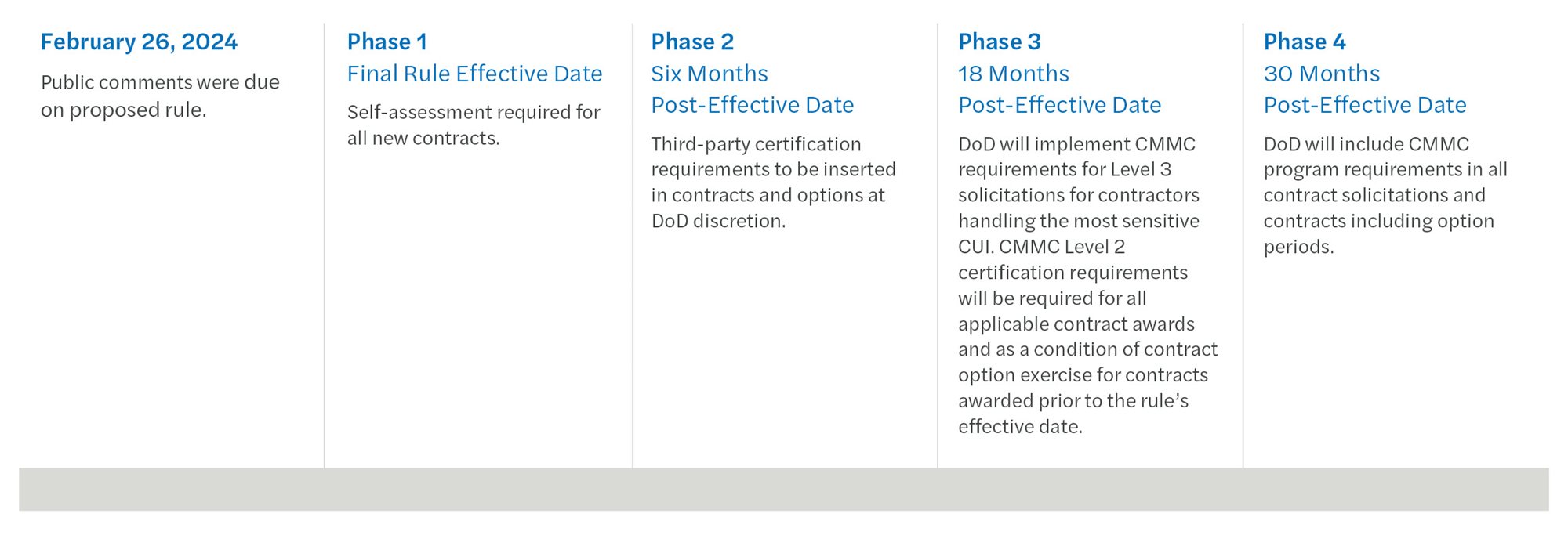
The Rollout of CMMC
Proposed Timeline
Full implementation of the CMMC program is dependent on the completion of federal rulemaking and, ultimately, the effective date of the planned CMMC final rule. As proposed, the phased implementation approach represents a more aggressive implementation timeline than anticipated. Key milestones contractors should be aware of include:
- February 26, 2024: Public comments were due on proposed rule.
- Phase 1–Final Rule Effective Date: Self-assessment required for all new contracts.
- Phase 2–Six Months Post-Effective Date: Third-party certification requirements to be inserted in contracts and options at DoD discretion.
- Phase 3–18 Months Post-Effective Date: DoD will implement CMMC requirements for Level 3 solicitations for contractors handling the most sensitive CUI. CMMC Level 2 certification requirements will be required for all applicable contract awards and as a condition of contract option exercise for contracts awarded prior to the rule’s effective date.
- Phase 4–30 Months Post-Effective Date: DoD will include CMMC program requirements in all contract solicitations and contracts including option periods.
Key Updates Noted in the Draft CMMC Rule
The proposed regulation is expansive; significant highlights identified by the CMMC compliance team at Forvis Mazars include:
- Annual Affirmations: Affirmations are explicit acknowledgements by senior leadership that all 110 requirements of NIST SP 800-171 are met by the organization. These affirmations are required concurrent with a C3PAO assessment or initial self-assessment, as well as annually thereafter.
- Plans of Action and Milestones (POAMs): Contractors that complete third-party assessments and do not meet all requirements will have the option to achieve Conditional Certification using POAMs. While they are helpful tools, POAMs cannot be over-relied upon for compliance. Contractors that do not meet at least 80% of CMMC requirements during the initial assessment are not eligible for the use of POAMs and all POAMs must be completed within 180 days of the end of the C3PAO assessment. C3PAOs will be required to validate that POAMs are closed with the 180-day Conditional Certification window. Additionally, controls included in CMMC Level 1, and those controls with the highest weighted values, may not be satisfied through POAMs.
- External Service Providers (ESPs): ESPs, such as Managed Service Providers (MSPs) that process, store, or transmit CUI, or Security Protection Data, must achieve the CMMC level equivalent to the contractors that they support.
- Joint Surveillance Voluntary Assessments (JSVAs): Existing NIST SP 800-171 assessments performed in coordination between the DIBCAC, a C3PAO, and the contractor will convert to CMMC certification upon rule implementation.
For further details, read our detailed analysis of the CMMC proposed rule here.
Certification Requirements & Approach
Within the proposed rule, DoD provides estimates of the number of entities subject to compliance at each level:
| Assessment Level | Small | Other than Small | Total | Percentage |
|---|---|---|---|---|
| Level 1 Self-Assessment | 103,010 | 36,191 | 139,201 | 63% |
| Level 2 Self-Assessment | 2,961 | 1,039 | 4,000 | 2% |
| Level 2 Certification Assessment | 56,689 | 19,909 | 76,598 | 35% |
| Level 2 Certification Assessment | 1,327 | 160 | 1,487 | 1% |
| Total | 163,987 | 57,299 | 221,286 | 100% |
| Percent | 74% | 26% | 100% |
Source: govinfo.gov
Who Performs the Certification Assessments?
C3PAOs are organizations that will be authorized to perform the CMMC assessments with oversight, training, and accreditation orchestrated by a civilian accreditation body, the CyberAB. Upon completion of final CMMC rulemaking, which is anticipated for 2024, C3PAOs will conduct a CMMC assessment and a certification will be issued to contractors that successfully meet all requirements.
Did You Know?
Forvis Mazars was among the first organizations accredited as an authorized C3PAO. As part of this process, Forvis Mazars underwent assessment from DoD’s assessment arm, DIBCAC.
Challenges in Preparing for CMMC Compliance

Common Challenges Met with Solutions in Preparing for CMMC
Challenge:
- System Security Plan Deficiences
- Lack of complete responses on how requirements are met for all in-scope sysems
- Lack of mapping between SSP and Policy/Procedure
Solution:
- Implement a System Security Plan
- Contractors should create and maintain an accurate System Security Plan (SSP) that describes the environment(s) used to process, store, or transmit CUI. The SSP should include a description of how each control requirement is met or not applicable to the system. To support an efficient assessment process, contractors should map supporting policy and procedure references within the SSP.
Challenge:
- Assignment of Roles and Responsiblities
- Control owners must be defined for each requirement
- Ongoing compliance requires security "buisness as usual"
- Coordination of assessment activities (point of contact)
Solution:
- Properly Assign Roles and Responsiblities
- Contractors should understand who will facilitate the assessment, and also identify key stakeholders that are able to demonstrate security requirement implementation during each assessment meeting. For smaller organizations, identification of key points of contact will be more straightforward than large organizations that maintain robust IT and Information Security functions.
Challenge:
- Correct Scoping
- Remain challenges around the definition of CUI
- Clearly Defining the CUI boundary
Solution:
- Understand the Scope
- It's imperative for your company to understand the scope as it pertains to CUI and define a boundary for CUI before moving forward with a CMMC assessment. Without a correct boundary in place, you run the risk of leaving out assets in the assessment, and the assessment itslef wont hold much value should something like a breach occur.
Challenge:
- Lack of Compliance Program
- No defined process within SDLC or otherwise to design new CMMC compliance systems
- CMMC compliance not baked into procurement processes
- Need to plan on how future updates to the SSP will occur
Solution:
- Prepare and Maintain a Compliance Program
- As a defense contractor, CMMC may be one of the first cybersecurity compliance frameworks for your organization. When preparing to stand up a compliance program, bring on a team who can help support your compliance program. In addition, have ongoing control management such as vulnerability scans and user access reviews once the assessment is complete.
Challenge:
- Technical Controls
- FIPS validated encyrption requires significant network restructuring and commonly causes functionality issues
- Cloud providers currently not FedRAMP moderate and are not willing to complete equivalency effors
Solution:
- Implement Robust Technical Controls
- To help protect CUI, implementing robust technical controls is commonly required. These changes may cause functionality issues when attempting to create a controlled eviornment. While putting technical controls into action, adequate planning and due diligence must be performed to ensure compatibility of solutions intended to meet compliance requirements and core business requirements.
Challenge:
- Navigating Cloud Service Provicers
- Lack of incorporation of Cloud Vendor CRMs
- Cloud providers currently not FedRAMP moderate without demonstrable equivalency
Solution:
- Cloud Service Providers:
- Contractors should be diligent in selecting cloud service providers for the transmission, processing, or storage of CUI. Existing DFARS 252.204-7012 requirements mandate that cloud services used to handle CUI meet requirements set forth by the federal risk and authorization management program (FedRAMP) Moderate level.
NIST SP 800-171 – The Foundation of CMMC
Overview of NIST SP 800-171 Revision 2
NIST SP 800-171 provides guidance on security controls to protect CUI processed, stored, or transmitted within nonfederal information systems. Released in 2020, adherence to Revision 2 of NIST SP 800-171 currently functions as a contractual requirement for DoD contractors and subcontractors.
The framework defines 110 security controls dispersed across 14 of the NIST SP 800-53 control families. Currently, DFARS 252.204-7012 requires contractors to maintain an SSP to define how each NIST SP 800-171 requirement is met, or how it will be met through defined POAMs.
What Are the NIST SP 800-171 Control Families?
- Access Control
- Media Protection
- Maintenance
- Incident Response
- Configuration Management
- Identification and Authentication
- Auditing and Accountability
- Personnel Security
- Awareness and Training
- Physical Protection
- Risk Assessment
- Security Assessment
- System and Communication Protection
- System and Information Integrity
Up to this point, compliance with NIST SP 800-171 has largely been validated through self-attestation. The CMMC program represents a more rigorous process to evaluate contractor’s cybersecurity capabilities through an independent third-party validation process. In advance of full-scale supply chain cybersecurity assessment capability that CMMC will offer DoD, the Defense Contractor Management Agency’s (DCMA) DIBCAC has performed NIST SP 800-171 assessments across a subset of the defense industrial base. DIBCAC has published reporting for the most commonly “Other Than Satisfied” requirements that provide contractors preparing for CMMC or NIST SP 800-171 assessment valuable feedback where resources may be best prioritized.
The Top 10 “Other Than Satisfied” NIST SP 800-171 Controls Include:
- 3.13.11, , Federal Information Processing Standards (FIPS)-validated cryptography [Systems and Communication Protection (SC)]
- 3.5.3, Multifactor Authentication [Identification and Authentication (IA)]
- 3.14.1, Identify, report, correct system flaws [System and Information Integrity (SI)]
- 3.11.1, Periodically assess risk [Risk Assessment (RA)]
- 3.11.2, Scan for vulnerabilities [Risk Assessment (RA)]
- 3.3.3, Review and update logged events [Audit and Accountability (AU)]
- 3.3.4, Audit logging process failure alerts [Audit and Accountability (AU)]
- 3.3.5, Audit record review, analysis, and reporting processes [Audit and Accountability (AU)]
- 3.6.3, Test incident response capability [Incident Response (IR)]
- 3.4.1, Establish/maintain baseline configuration [Configuration Management (CM)]
Future Consideration: NIST SP 800-171 Revision 3
On May 10, 2023, NIST released a draft version of Revision 3 for SP 800-171, the foundational framework of requirements for protecting CUI. The new revision is still in draft form, so final requirements could look different. It also is unclear when the final version of the document will be released and how it will be adopted.
While still in draft form, the changes introduced will require organizations to consider how their CUI protection programs need to be modified. Organizations that maintain contracts with DoD or may be preparing for CMMC compliance will need to consider incorporating these new requirements into their CUI protection and cybersecurity programs.
The CMMC proposed rule specifically cites NIST SP 800-171 Revision 2 as the current requirement for contractors, and contractors should focus primary compliance efforts on meeting existing requirements. A transition timeline or details on how new revisions of NIST SP 800-171 will be incorporated into the CMMC program is currently unclear. It is clear that one of NIST’s primary objectives with the revision was to enhance consistency between SP 800-171 and the more expansive SP 800-53 Revision 5. As such, 49 controls were identified as containing “Significant Changes” per NIST’s published analysis. Below are the top five new requirements we believe may most affect organizations subject to SP 800-171 compliance.
- Supply Chain Risk Management is an area of emphasis in newly introduced requirements. At least five of the 26 proposed control additions are supply chain-oriented. The new requirements would mandate that organizations establish a third-party risk management program that:
- Requires external service providers to adhere to organizational security requirements
- Establishes a monitoring function to assess external service provider compliance with organizational security requirements
- Establishes requirements for development or acquisition of new system components
- Uses acquisition strategies or contractual tools to mitigate supply-chain risks
- Maintains a process for ongoing identification of supply chain weaknesses or deficiencies
- Information Location: Sometimes referred to as a “data inventory,” the specific location of CUI will need to be clearly identified and documented. Organizations should maintain an inventory of system locations where CUI is processed or stored, and the user groupings with access to those locations will need to be clearly identified.
- Policies & Procedures: Already an existing backbone of a strong cybersecurity program, the proposed changes would formalize requirements for organizations to periodically review, approve, and disseminate cybersecurity policies and procedures.
- Independent Assessment: Similar to other predominant technology frameworks, including ISO 27001 and SOX 404(a), a requirement for an independent assessment function, such as internal audits, is planned to be incorporated as a part of NIST SP 800-171 Revision 3. Organizations would need to use independent resources to periodically assess control implementation. However, unlike other frameworks, no required cadence for the independent assessments is defined.
- Unsupported System Components: System components that may be end-of-life or otherwise unsupported by the developer or manufacturer with security patches increase the risk that a system can be compromised by a malicious actor. The new revision would require that these unsupported components be replaced or otherwise mitigated through extended support agreements or in-house developed solutions.
The Future of CMMC
How Does This Impact Other Federal Agencies & Cybersecurity Regulation?
Safeguarding CUI is a top priority with federal cybersecurity efforts. In June 2023, the Department of Homeland Security (DHS) published a final ruling, “Safeguarding of Controlled Unclassified Information,” with further guidelines for safeguarding CUI. Vetting requirements are now being enforced for employees so that access is only provided to those who need CUI. The DHS CUI rule does not require third-party assessment at this time; however, this development demonstrates that DoD is trailblazing a sweeping approach to supply-chain cybersecurity that could ultimately spread to federal civilian agencies.
Federal cybersecurity frameworks existed before CMMC and may create confusion for contractors in understanding what their existing requirements are. Significant federal cybersecurity frameworks include:
- FedRAMP
- The FedRAMP initiative was established in 2011 and is maintained by the FedRAMP Project Management Office (PMO) in the General Services Administration. The program is intended to provide a cost-effective risk-based approach for federal agencies to adopt and use cloud services. The program requires that cloud service providers (CSPs) that desire to do business with federal agencies achieve a specific FedRAMP certification and authorization level.
- FISMA
- The Federal Information Security Management Act (FISMA) is a federal law that defines a comprehensive framework for securing federal information systems and data. It relies on FIPS 200 for minimum security controls. While it is specifically applicable to federal systems, many agencies have required their service providers to demonstrate compliance with the FISMA standard.
- Other Common Standards
- Many industries incorporate common cybersecurity controls, standards, and best practices such as ISO 27001, the Payment Card Industry, and HITRUST. Aligning with these standards may help organizations in industry-specific practices comply even further with CMMC, as they may share common security principles. However, because these standards are tailored for a specific industry, and often specific data types, they do not automatically translate into CMMC compliance.
The Impact on FedRAMP & Cloud Providers
Similar to CMMC, FedRAMP is divided into three levels based on the type of information a cloud solution will process, store, or transmit. While significant overlap exists between CMMC and FedRAMP, a mechanism for FedRAMP-certified cloud providers to automatically assert CMMC compliance remains unclear.
FedRAMP requirements are still relevant to contractors that are not providing cloud services to DoD. As codified by the CMMC proposed rule, and previously within DFARS 252.204-7012, contractors must only utilize FedRAMP Moderate Authorized or equivalent cloud service providers for the processing, storage, or transmission of CUI.
Given uncertainties of how cloud providers may evidence FedRAMP equivalence, as underscored by a recent DoD CIO Memo, contractors should verify that cloud services intended for usage with CUI are listed as authorized at the Moderate level on the FedRAMP Marketplace.
Joint Surveillance Voluntary Assessment (JSVA) Program
This program offers contractors the chance to demonstrate compliance with CMMC requirements through a joint assessment performed by a C3PAO and DoD’s DIBCAC. The proposed rule stipulates that contractors who successfully complete a joint surveillance assessment, and meet all requirements are eligible for formal CMMC certification at the completion of rulemaking.
- Two Assessments in One: Joint surveillance assessments are concurrent assessments based upon NIST SP 800-171, performed by DIBCAC and C3PAOs. A DIBCAC High Confidence Assessment is an assessment performed at DIBCAC’s discretion of any contractor in the defense supply chain. By undergoing a joint surveillance assessment, a contractor may avoid being surprised by an unexpected DIBCAC assessment notice later.
- Competitive Advantage: Undergoing a joint surveillance assessment demonstrates a contractor’s commitment to both its federal defense customer(s) and the protection of sensitive CUI it handles on the government’s behalf. Demonstrating this early commitment can help make contractors more appealing in the marketplace.
- Be Prepared When CMMC Becomes a Requirement: When CMMC becomes a contract requirement, there’s expected to be a rush for certification assessment and a limited number of authorized assessment firms. Depending upon how the final CMMC rule is structured, getting in front of this potential bottleneck by having undergone an assessment with both DIBCAC and a C3PAO can better position a contractor to be ready to pursue full CMMC certification.
For further details, read our article on Changes to the Implementation Timeline of CMMC.
As the CMMC leader at Forvis Mazars, what is your take on CMMC and why should contractors move forward with Readiness and consider the JSVA Program?
“Forvis Mazars performed several of the first JSVAs and is currently a leader in the projects. We have developed an efficient approach to collaboration with our contractor clients and DIBCAC to conduct efficient and timely assessments. We certainly recommend any contractors that believe they are ready for CMMC Level 2 compliance to consider a JSVA to be early to market with critical initiative.” – Tom Tollerton, Principal and CMMC Certified Assessor
FAQs About CMMC
Our team at Forvis Mazars can help determine preparedness to undergo a CMMC certification assessment.
As the sixth authorized C3PAO, Forvis Mazars is an industry leader for NIST SP 800-171 compliance and CMMC readiness consulting services. Our firm has an experienced team composed of CMMC-certified professionals and certified assessors providing tailored services to help meet contractor needs. We can help contractors anticipate potential compliance issues, provide resources, and share the following support:
- NIST SP 800-171 Joint Surveillance Assessments (C3PAO Services)
- CMMC Joint Surveillance Assessments (C3PAO Services)
- Readiness Assessments & Gap Analyses
- SSP & Policy Assistance
- vCISO & Project Management
- Security Program Design & Consulting
- Third-Party & Supply Chain Risk Management Advisory Consulting
- Offensive Security Assessments
Ready to become CMMC-compliant or undergo assessment? Contact our CMMC professionals at Forvis Mazars today!

Tom Tollerton, CISSP, QSA, CMMC-CCA | Principal | 704.367.7061 | tom.tollerton@us.forvismazars.com

Alex Imani, CISSP, CISA, CMMC-CCA | Manager | 704.367.7093 | alex.imani@us.forvismazars.com