In this article, we’ll show how to use Microsoft Azure Logic Apps (LA) to securely obtain the session ID and temporary endpoint URL needed for a Sage Intacct application programming interface (API) call.
In general, an API call has three parts: the request the company/user submits, the retrieval of the requested information, and the delivery of that information from the source system/server to the company/user.
We’ll walk through a scenario where a webhook is being used to receive a response from a source system. Here we'll show what’s needed to make a call to the Sage Intacct API to obtain a session ID and temporary endpoint.
When an API call is completed successfully, users can log into the source system without needing to re-authenticate for the duration of that session.
Initialize LA Variables
To get started, we’ll perform a series of steps to initialize a number of “string” variables. We’ll use a naming convention that adds “v” as a prefix to all variable names. In addition, we’ll use descriptive names for all actions. See the example below.
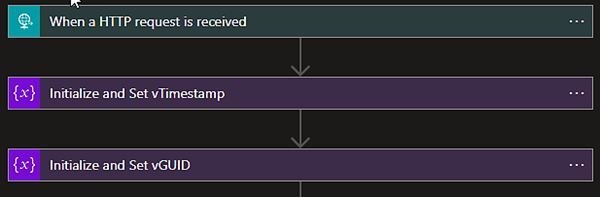
Obtain Key Vault Keys
To verify the usernames and passwords used when making the call to Sage Intacct, we’ll use Microsoft Azure Key Vault. Key Vault has a prebuilt connector that works well with LA.
First, add a Key Vault connector to the LA Designer. Select the “Get Secret” action under the Key Vault connector. Note: If it’s your first time using Key Vault with LA, you’ll be required to authenticate with your preferred approach, e.g., OAuth 2.0/service principal.
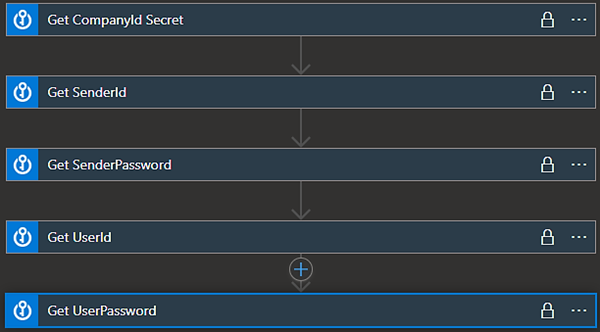
Then, you’ll select the Key Vault that contains your keys. (Here’s how to create a Key Vault if this hasn’t been done already.) Next, select the appropriate Key Vault secret. Immediately following the retrieval of the secret from the Key Vault, add the “Set Variable” connection and set the corresponding variable to the value just retrieved from the Key Vault.
You’ll repeat this process for each of the secrets you’ll need to retrieve from the Key Vault. In this example, we’ll use secrets for:
- CompanyID
- SenderID
- SenderPassword
- UserID
- UserPassword
Secure Key Vault Values
Once you’ve completed this setup, click on the ellipse for each Key Vault action and select “Settings.”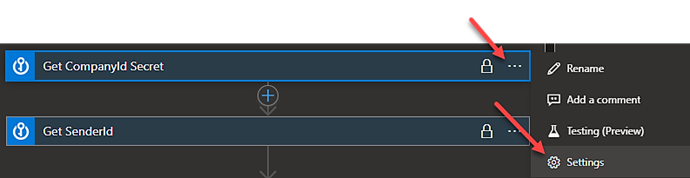
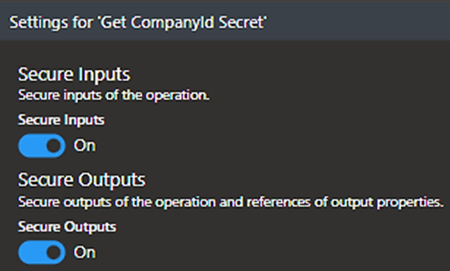
Use the toggle buttons to turn on Secure Inputs and Secure Outputs. This hides from view any values LA retrieves and returns. Click “Done” to complete this step for each secret value.
HTTP – POST Session ID
The last step in the process is to employ the HTTP Request connector. Sage Intacct documents how the XML must be structured when making an initial call.
When setting up the HTTP call, follow the information below:
- Method: POST
- URI: https://api.intacct.com/ia/xml/xmlgw.phtml
- Headers:
- Key: Content-Type
- Value: application/xml
- Body:

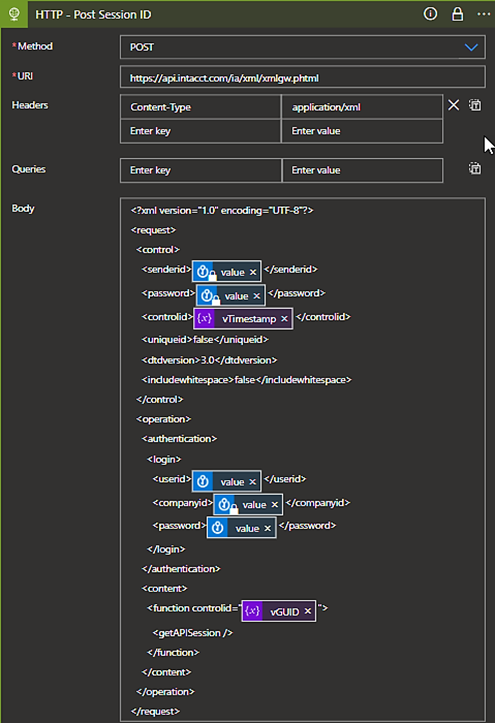
Retrieve Session ID & Temporary Endpoint
Once the call is made using the HTTP connector, the session ID and the temporary endpoint will be returned in the body of the HTTP request in XML format. To collect this information, you’ll need to execute a series of three Compose Actions.
The first Compose Action will add the “Body” returned from the HTTP call as input.
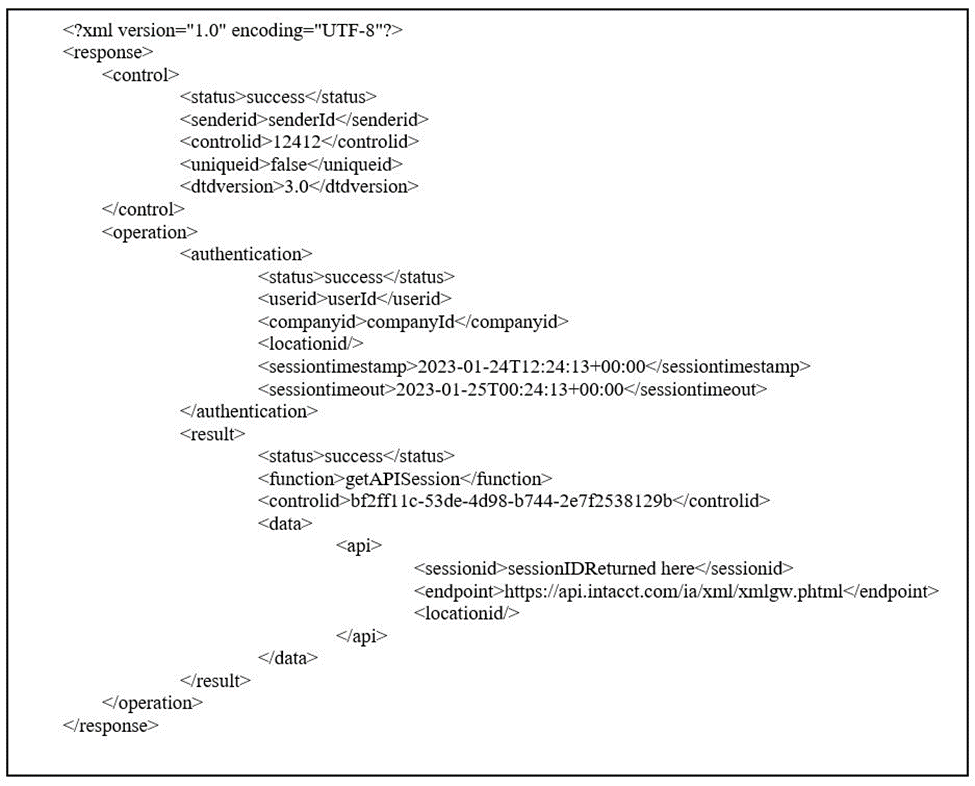
Below is an example of the XML response:
Second, you’ll need to retrieve the session ID. We’ll use the XPath function to find the exact value we’re looking for within the Body response.
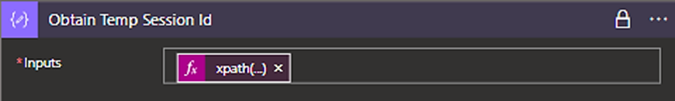
Using the Dynamic Content, build the following: xpath(xml(outputs('Retrieve_Post_Session_ID_Body')),'string(/response/operation/result/data/api/sessionid)')
The output 'Retrieve_Post_Session_ID_Body' is the name of the Compose Action built from the previous Compose Action.
Lastly, we’ll need to follow the same process to retrieve the temporary endpoint.
Using the Dynamic Content, build the following: xpath(xml(outputs('Retrieve_Post_Session_ID_Body')),'string(/response/operation/result/data/api/endpoint)')
The key difference between the second and third Compose Actions is the node we’re trying to access—“sessionid” versus “endpoint.”
How Forvis Mazars Can Help
The tips in this article are meant to help with Sage Intacct session authentication using the Microsoft Azure platform. For more developer tips or support services, use the Contact Us form below to get in touch.
The Insights & Automation team at Forvis Mazars can help organizations use technologies to gain efficiencies in business processes and meet an ever-changing landscape. Service offerings include business intelligence and Microsoft Power Platform assessments, along with software implementations and app-to-app integrations. We are a Sage Partner, Microsoft Dynamics Gold Partner, and 2022-23 recipient of the Microsoft Inner Circle award, in addition to the Solver Evangelist of the Year award.
